Azure Security Center
Azure Security Center is a service that helps keep your computer systems safe, both in the cloud (like on Azure) and in your own data centers.
Security Recommendations
It gives you advice on how to improve your security settings to make your systems more secure.
Detect and Block Malware
It watches out for harmful software (malware) and stops it from causing damage.
Analyse and Identify Potential Attacks
It looks for signs that someone might be trying to attack your systems and helps you take action to prevent it.
Just-in-time Access Control for Ports
It controls access to certain parts of your system (called ports), only opening them when needed and closing them otherwise, to reduce the risk of unauthorized access.
Capabilities
Azure Security Center offers a range of capabilities to help maintain and enhance the security of your cloud and on-premises resources.
Policy Compliance You can create and enforce security policies that apply to multiple groups, subscriptions, or entire organizations to ensure consistent security practices.
Continuous Assessments It continuously checks your resources (both new and existing) to make sure they are set up securely and correctly.
Tailored Recommendations It provides personalized suggestions on how to improve security based on your current setup, including step-by-step instructions.
Threat Protection It monitors for potential threats and provides alerts along with detailed reports on which resources are affected, helping you to quickly respond and mitigate risks.
Azure Sentinel
Azure Sentinel is a powerful tool that helps organizations manage and respond to security threats. It combines security information and event management (SIEM) with security orchestration, automation, and response (SOAR).
- SIEM: Collects and analyzes data from across your enterprise to identify potential security threats.
- SOAR: Automates responses to security threats, making it easier and faster to handle incidents.
Connectors and Integrations
Office 365: Integrates with Office 365 to monitor and protect your email and productivity tools. Azure Active Directory: Works with Azure Active Directory to keep an eye on user access and identity management. Azure Advanced Threat Protection: Connects with Azure Advanced Threat Protection to detect and respond to advanced threats. Microsoft Cloud App Security: Integrates with Microsoft Cloud App Security to protect your cloud applications and data.
Azure Key Vault
Azure Key Vault is a service that helps you securely store and manage sensitive information like passwords, keys, and certificates in a centralized cloud location.
Secrets Management
Securely stores and manages sensitive information such as passwords, connection strings, and API keys.
Key Management
Handles encryption keys used to encrypt and decrypt your data, ensuring they are stored securely and accessed only by authorized applications.
Certificate Management
Manages SSL/TLS certificates, allowing you to provision, manage, and deploy certificates for your applications and services.
Storing Secrets Backed by Hardware Security Modules (HSMs)
Ensures that secrets are stored with the highest level of security by using hardware security modules, which provide a physical layer of protection.
Azure Dedicated Host
Azure Dedicated Host provides dedicated physical servers for your Azure virtual machines (VMs), ensuring that these servers are exclusively used by your organization.
Hardware Isolation at the Server Level
The physical server is dedicated to your organization, providing enhanced security and performance by isolating your workloads from those of other customers.
Control Over Maintenance Event Timing
You have the ability to control when maintenance events, such as updates or reboots, occur on your dedicated servers. This allows you to schedule maintenance during times that are least disruptive to your operations.
Aligned with Azure Hybrid Use Benefits
You can use your existing Windows Server and SQL Server licenses with Azure, maximizing your investments and potentially reducing costs.
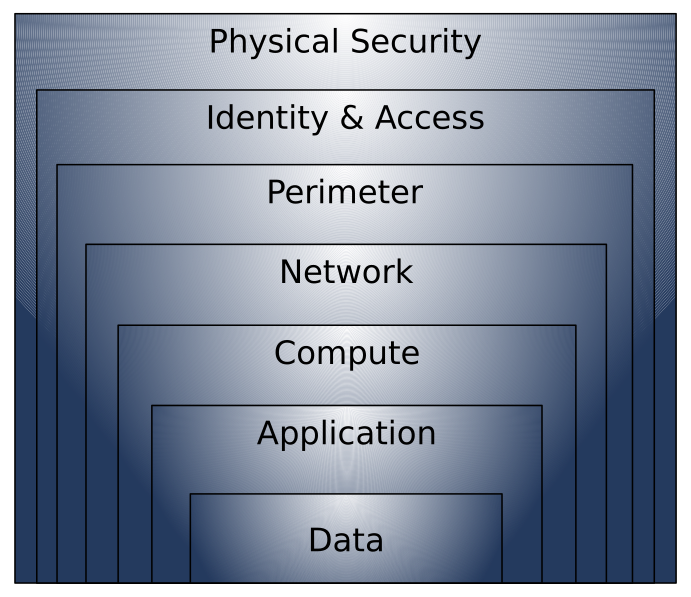
Defense in Depth
Defense in Depth is a security strategy that uses multiple layers of protection to secure computer systems.
A Layered Approach to Securing Computer Systems
Security measures are implemented in multiple layers, rather than relying on a single defense mechanism.
Provides Multiple Levels of Protection
Each layer adds an extra level of security, making it harder for attackers to breach the system.
Attacks Against One Layer Are Isolated from Subsequent Layers
If an attacker manages to get through one layer, the other layers still provide protection, limiting the overall impact of the attack.
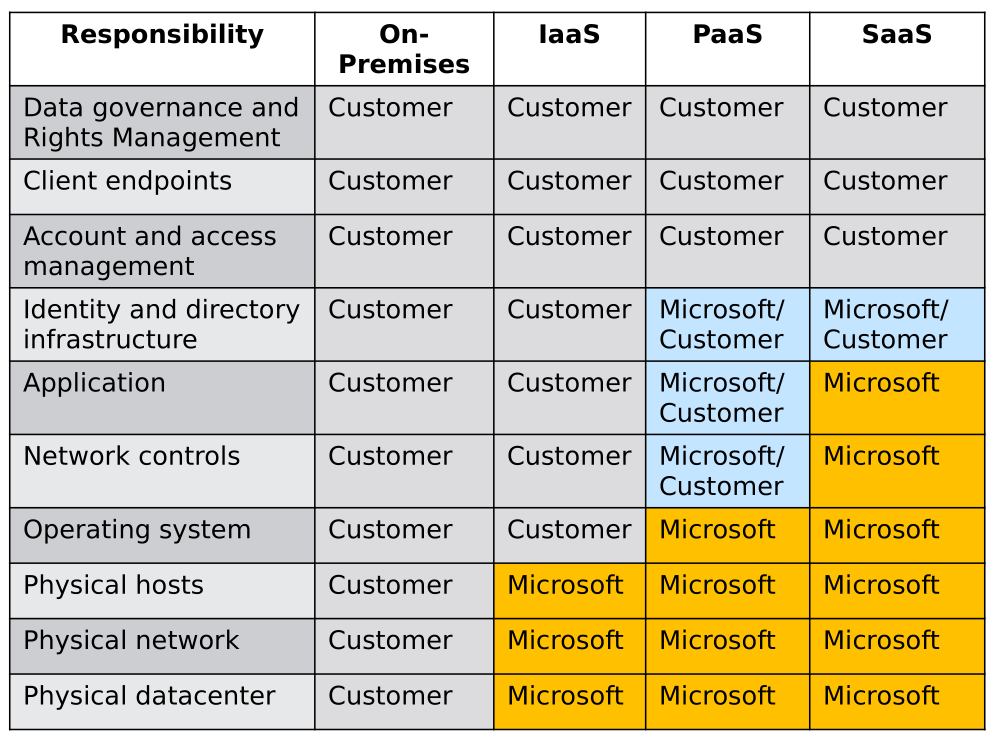
Shared Security
Shared Security is a concept that defines the division of security responsibilities between cloud providers and their customers.
- When you move your IT infrastructure from your own data centers to the cloud, some of the security responsibilities are transferred to the cloud provider.
- Both the cloud provider and the customer have specific roles in maintaining security:
- Cloud Provider's Responsibilities: Securing the underlying infrastructure, such as physical servers, networks, and storage, as well as ensuring the security of the cloud platform itself.
- Customer's Responsibilities: Securing their own data, managing user access, and configuring their applications and services securely.
Network Security Groups
Network Security Groups (NSGs) are used to control the flow of network traffic to and from Azure resources within an Azure Virtual Network. Here's a simple explanation of their key features:
Set Inbound and Outbound Rules
You can create rules to filter network traffic based on criteria such as source and destination IP addresses, port numbers, and protocols.
Add Multiple Rules
You can add as many rules as needed within the limits of your Azure subscription to fine-tune the network traffic filtering.
Default Security Rules
Azure automatically applies a set of default security rules to new NSGs to provide baseline protection.
Override Default Rules
You can create new rules with higher priority to override the default rules, allowing for customized security configurations that meet your specific needs.
Azure Firewall
Azure Firewall is a managed firewall service that helps protect your Azure Virtual Network resources.
- It's a stateful firewall, which means it can keep track of the state of active connections and make decisions based on that state.
- Azure Firewall can filter both inbound and outbound traffic, allowing you to control which traffic is allowed to enter or leave your virtual network.
- It provides high availability by distributing traffic across multiple instances of Azure Firewall, ensuring your network remains protected even if one instance fails.
- Azure Firewall can scale up or down based on your traffic needs, providing the flexibility to handle varying levels of network traffic.
- It integrates with Azure Monitor for logging and analytics, allowing you to monitor and analyze firewall traffic and security alerts.
Additionally, Azure Application Gateway provides a Web Application Firewall (WAF) for protecting web applications. WAF provides centralized, inbound protection against common web-based attacks such as SQL injection and cross-site scripting (XSS).
Azure Distributed Denial of Service (DDoS) protection
DDoS (Distributed Denial of Service) attacks aim to disrupt online services by overwhelming them with traffic.
- DDoS attacks can make applications slow or unresponsive by flooding them with more traffic than they can handle.
- Azure provides DDoS protection by sanitizing unwanted network traffic before it reaches your Azure resources, helping to ensure that legitimate traffic can still access your services.
- The Basic service tier of DDoS protection is automatically enabled for all Azure resources, providing a baseline level of protection.
- The Standard service tier adds additional mitigation capabilities that are specifically tuned to protect Azure Virtual Network resources, providing enhanced protection against DDoS attacks.

Defense in Depth Reviewed
- Network Security Groups (NSGs) and Azure Firewall can be used together to achieve a layered approach to network security. NSGs can provide basic traffic filtering at the networking layer, while Azure Firewall can provide more advanced filtering and threat protection at the application layer.
- Azure DDoS Protection and Azure Firewall can be used together to protect your network boundaries. Azure DDoS Protection helps mitigate DDoS attacks, while Azure Firewall provides additional protection against unauthorized access and threats.
- NSGs are used to control inbound and outbound traffic between networked resources. By configuring NSG rules, you can restrict traffic to only allow communication that is necessary for your network.